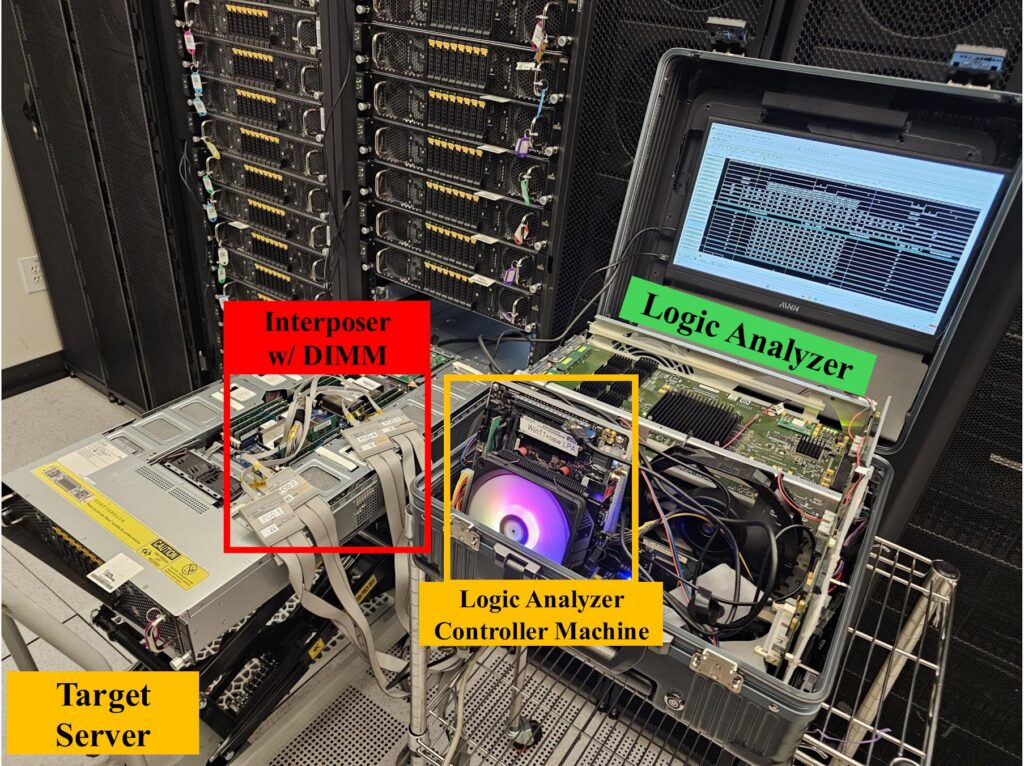
Cheap, fast and the size of a briefcase.
“Now that we have interposed DDR5 traffic, our work shows that even the most modern TEEs from all vendors with available hardware are vulnerable to cheap physical attacks,” Genkin said.
The equipment required by TEE.fail works with commercially available equipment that costs less than $1,000. One of the devices the researchers built fits into a 17-inch briefcase, so it can be smuggled into a facility that houses a TEE-protected server. Once the physical attack has been carried out, it is not necessary to reconnect the device. Attackers who break TEE on the servers they operate do not need to be stealthy, allowing them to use a larger device, which the researchers also built.
Equipment that connects to the DIMNM.
An overview of the equipment involved.
The researchers demonstrated attacks against a variety of services that rely on chip manufacturers’ TEE protections. (For ethical reasons, the attacks were carried out against identical but separate infrastructure from the targets’ networks.) Some of the attacks included BuilderNet, dstack, and Secret Network.
BuilderNet is a network of Ethereum block creators that uses TDX to prevent parties from spying on each other’s data and to ensure fairness and that the test coin is redistributed honestly. The network builds blocks worth millions of dollars every month.
“We demonstrated that a malicious operator with a certification key could join BuilderNet and obtain configuration secrets, including the ability to decrypt sensitive order flow and access the Ethereum wallet for payment validators,” the TEE.fail website explained. “Furthermore, a malicious operator could create arbitrary blocks or execute first (i.e., construct a new transaction with higher fees to ensure theirs executes first) sensitive transactions for profit while offering deniability.”
To date, the researchers said, BuilderNet has not provided mitigations. Attempts to contact BuilderNet officials were unsuccessful.
data stack is a tool for creating confidential applications that run on virtual machines protected by Nvidia Confidential Compute. Researchers used TEE.fail to forge certifications certifying that TDX performed a workload using Nvidia protection. He also used “borrowed” certifications to misrepresent ownership of GPUs trusted by an unsuspecting party.